Configure live stream repeater applications in Wowza Streaming Engine™ media server software. A live stream repeater is an origin-edge server configuration for delivering a single live stream across a multiple-server deployment to many viewers. The source stream is published to an origin server, and the stream is made available for playback on multiple edge servers.
Video tutorial: Configure a live stream repeater
See how to configure origin and edge servers as a live stream repeater in Wowza Streaming Engine Manager.
1. Configure the origin server(s)
First, configure the origin server that you will send the source stream to for delivery to the edge server.
Note: For testing purposes, you can configure a single instance of Wowza Streaming Engine as both the origin server and edge server if you do not publish your stream using a .stream file and MediaCaster (re-streaming). If you configure both servers with a single Wowza Streaming Engine instance, the [wowza-origin-address] and [wowza-edge-address] values are the same.
- In Wowza Streaming Engine Manager, click the Applications tab and then click Add Application.
- On the Add Application page, click the Live application type.
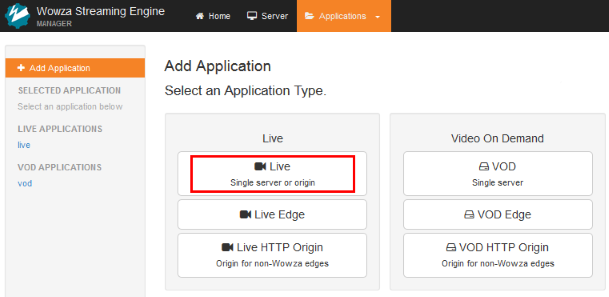
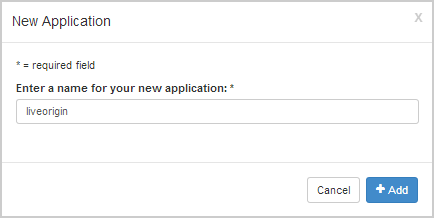
- In the New Application dialog box, enter a name for the origin application, such as liveorigin, and then click Add.
- From the application page, under Playback Types, select Adobe RTMP and any other playback protocols you need.
Important: The Adobe RTMP playback type must be set to enable edge servers to connect to the origin server in a live stream repeater configuration.
- Click Save.
2. Configure the edge server(s)
- In Wowza Streaming Engine Manager, click the Applications tab and then click Add Application.
- On the Add Application page, click the Live Edge application type.
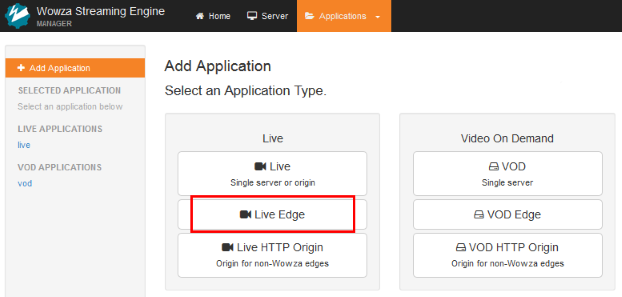
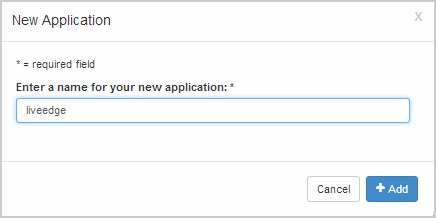
- In the New Application dialog box, enter a name for the edge application, such as liveedge, and then click Add.
- From the application page, under Playback Types, select any playback protocols you need.
- For Primary Origin URL, enter the URL of the Wowza Streaming Engine origin server. The URL must use one of the following protocol prefixes: wowz://, wowzs://, rtmp://, or rtmps://.
- (Optional) For Secondary Origin URL, enter the URL of a second Wowza Streaming Engine origin server, if you have one, as a backup for redundancy. If the primary origin server fails, clients may experience up to a 12-second timeout before failover to the backup origin server is completed. Use a secondary origin only for failover purposes. The URL must use one of the following protocol prefixes: wowz://, wowzs://, rtmp://, or rtmps://.
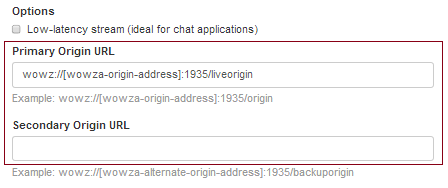
About using WOWZ and WOWZS
The WOWZ™ protocol is a TCP-based messaging protocol used for server-to-server communication and is enabled by default. If one of the Wowza Streaming Engine servers in the origin-edge configuration is running an earlier version of the software, an RTMP connection is established between the servers instead.
If you specify that the wowzs:// URL prefix is used to address the origin server over an SSL connection, be aware of the following requirements for SSL encryption:
- The SSL certificate must be from a certificate authority (see Request an SSL certificate for Wowza Streaming Engine from a certificate authority). Self-signed certificates aren't supported. Wowza StreamLock™ certificates are fully supported (see Get SSL certificates from the Wowza Streaming Engine StreamLock service).
- You must specify the domain name when addressing the origin server. The origin IP address can't be used.
- If you don't specify a port value when addressing the origin server, port 443 is used.
- The live stream repeater will fail to connect to a non-SSL-protected destination port on the origin server. It will repeatedly try to connect. Connection failures like the following will be reported in the Wowza Streaming Engine logs:
WARN server comment - LiveMediaStreamReceiver.secureConnectionValidation: SSL Connection was not established: wowzs://[wowza-ip-address]:1935/myApplication/_definst_/myStream
Each stream that's played through this application uses the primary and secondary origin URL values to locate the Wowza Streaming Engine origin server for the stream.
3. Publish the source stream
After configuring the origin and edge servers, publish a live stream to the application on the Wowza Streaming Engine origin server. Refer to the following resources for help with publishing a live stream from various cameras and encoders to the Wowza Streaming Engine origin server:
Note: When re-streaming, playback on the edge server fails if a .stream file on the edge server has an identical name to the source .stream file on the origin server, so ensure that there are no .stream files on the edge server with the same name as .stream files on the origin server.
4. Test playback
To test the live stream repeater configuration, play the stream from the edge server using the application you created on the edge server and the edge server address. With the Wowza Streaming Engine instance on the edge server, complete the following steps.
- From your edge application's page in Wowza Streaming Engine Manager, click Test Playback.
- Review and, if needed, edit the following information in the Test Playback window for your stream:
- Server – The IP address or domain name of the server and the streaming port ([address]:[port]).
- Stream – The name of the stream published to the origin server.
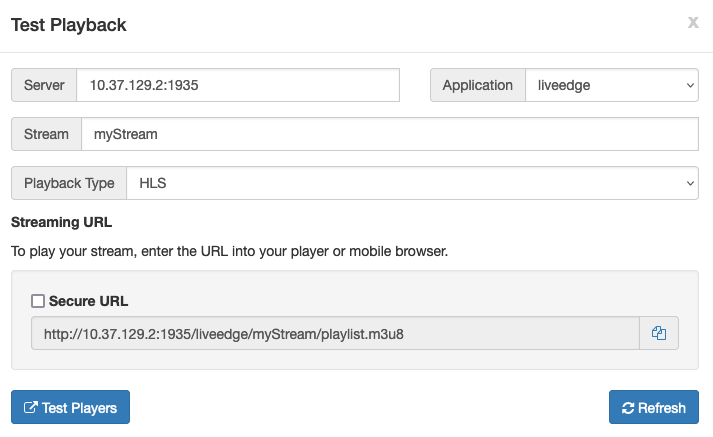
- (Optional) In the Streaming URLs section, select Secure URL for the streaming protocol you want to use to test playback if you have configured SSL/TLS for streaming over https, rtmps, or rtsps.
- Click the Copy icon for the streaming protocol you want to use to test playback.
- Paste the playback URL into your player or a mobile browser depending on the protocol. Alternatively, you can use the Wowza Video Test Players webpage.
For more information about playback URLs, see About playing Wowza Streaming Engine streams.
(Optional) Secure a live stream repeater
Learn how you can secure a live stream repeater configuration using SecureToken or MPEG-DASH CENC encryption.
Secure the origin-edge configuration with SecureToken
You can prevent unauthorized re-streaming from edge servers and direct streaming from clients using SecureToken.
Note: The shared secret values used in this section are sample values for the purposes of the tutorial. Be sure to replace them with your own custom values when deploying your live stream repeater (origin/edge) configuration in production environments.
1. Secure the origin server(s)
Complete the following steps in Wowza Streaming Engine Manager on the origin server.
- In the Applications contents panel under liveorigin, click Playback Security and then click Edit.
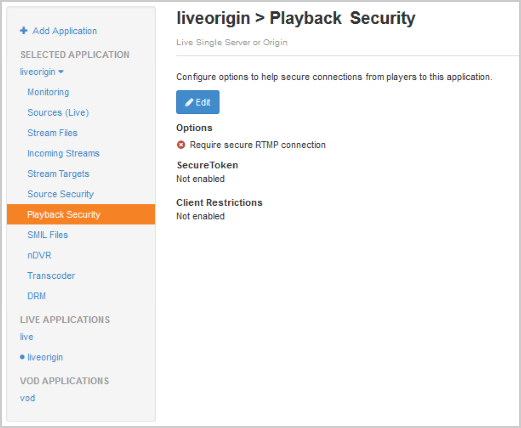
- Configure the following settings:
- Under SecureToken, select Protect RTMP protocol using TEA (SecureToken version 1) as the type of secure token playback protection to use.
- Enter an alphanumeric token value in the Shared Secret box, or click Generate SecureToken Shared Secret to generate a random alphanumeric token in the box. This value must be used by all Wowza edge servers and RTMP players that connect to this application. If the tokens don't match or aren't set, then the connection is rejected.
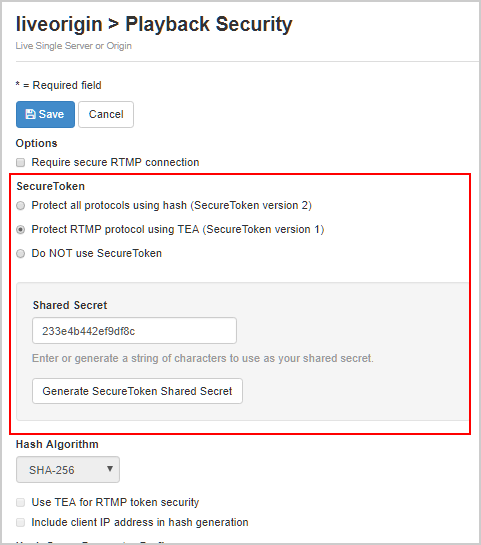
- Click Save.
2. Secure the edge server(s)
Complete the following steps in Wowza Streaming Engine Manager on each edge server.
- In the Applications contents panel, under liveedge, click Source Security and then click Edit.
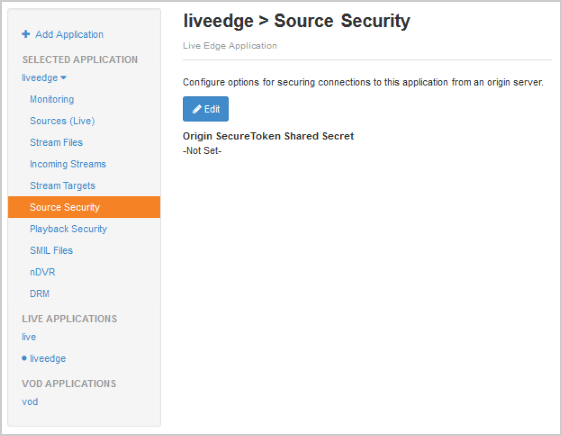
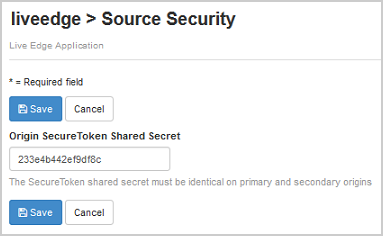
- In the Source Security dialog box, enter the Origin SecureToken Shared Secret that you generated when securing the origin, and then click Save. This setting enables this Wowza edge server to connect to the secure Wowza origin server.
- To use Secure Token functionality on the edge server to prevent unauthorized direct streaming, in the contents panel, click Playback Security and then click Edit.
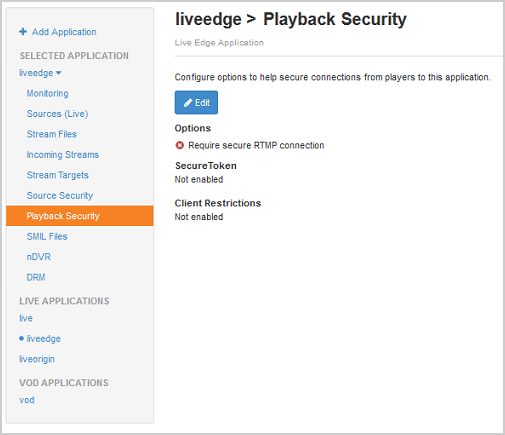
- Configure the following settings:
- Enter an alphanumeric token value in the Shared Secret box, or click Generate SecureToken Shared Secret to generate a random alphanumeric token in the box. This value must be used by all Wowza edge servers and RTMP players that connect to this application. If the tokens don't match or aren't set, then the connection is rejected.

- Enter an alphanumeric token value in the Shared Secret box, or click Generate SecureToken Shared Secret to generate a random alphanumeric token in the box. This value must be used by all Wowza edge servers and RTMP players that connect to this application. If the tokens don't match or aren't set, then the connection is rejected.
For more information about configuring SecureToken options, see Protect streaming using SecureToken in Wowza Streaming Engine.
Encrypt MPEG-DASH streams with CENC
Common Encryption (CENC) can be applied to MPEG-DASH streams sent through a live stream repeater configuration. The origin instance is configured to acquire the encryption keys, and the MPEG-DASH chunks are built and encrypted on the edge instances.
This requires that the AES-128 encryption keys used in the CENC encryption are sent from the origin to the edge instances. Wowza Streaming Engine performs an extra encryption on the key information to secure this transmission with the liveRepeaterEncryptionSharedSecret property. This property provides a unique encryption key for each stream served by the origin. The default shared secret can be used, or you can define your own Custom Property on the application properties page.
Note: When defining a custom shared secret value, be sure define the same property/value on all origin and edge instances to ensure correct operation.
- In Wowza Streaming Engine Manager, click the Applications tab and select your application in the contents panel.
- In the details page, click the Properties tab, and then click Custom in the Quick Links bar.
- In the Custom section, click Edit.
- Click Add Custom Property, specify the following settings in the Add Custom Property dialog box, and then click Add:
- Path - Select /Root/Application
- Name - Enter liveRepeaterEncryptionSharedSecret
- Type - Select String
- Value - Enter your shared secret.
- Click Save, and then restart the application when prompted to apply the changes.
The property is added to the application's Application.xml file within the <Application>/<Properties> container element as in the following example:
<Property> <Name>liveRepeaterEncryptionSharedSecret</Name> <Type>String</Type> <Value>[mySecret]</Value> </Property>
















